Like an Intrusion detection system (IDS), an Intrusion prevention system (IPS) screens network traffic. In this article, we deep dive into Intrusion Prevention System architecture.
An Intrusion Prevention System (IPS) is a framework that screens a network for evil exercises, for example, security dangers or policy compliance.
Vulnerability exploits normally come in the form of malicious inputs to an objective application or resources that the attacker uses to block and pick up control of an application or System.
For instance, an IPS may drop a packet that it decides to be noxious and hinder all further activity from that IP address or port, although there is no impact on genuine traffic.
Intrusion prevention systems are considered incremental since they both screen the network traffic and system activities for malicious activity.
The fundamental contrasts are dissimilar to an Intrusion detection system, Intrusion prevention systems are set in line and can effectively anticipate or hinder intrusions that are recognized.
Table of contents – Intrusion Prevention System
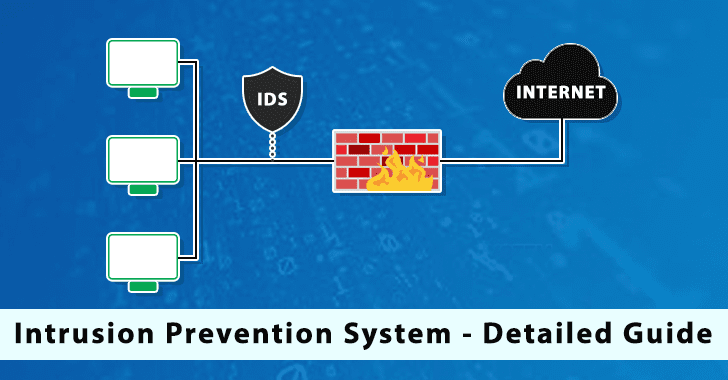
Intrusion Prevention System Architecture
At the heart of an intrusion prevention system deployment is one or more sensors. Each sensor is strategically positioned to monitor traffic for particular network segments.
Organizations used to deploy a sensor for each network segment, but now a single sensor can monitor several network segments simultaneously.
You can Enroll in the SOC Analyst – Cyber Security Intrusion Training Course which gives a detailed SIEM tool for monitoring and analysis of the cyber attack.

In order to monitor key network segments throughout an organization, IPS sensors are often deployed wherever networks with different security policies connect, such as Internet connection points, or where internal user networks connect to internal server networks.
In addition to hardware appliance sensors, some vendors also offer virtual appliance sensors.
These have the same monitoring and analysis capabilities as hardware appliance sensors, but the virtual appliance is designed for deployment within a server that runs virtual machines (VMs) to monitor the virtual networks between those VMs.
In such an architecture, a virtual appliance on the server is necessary because network traffic between VMs will not travel outside the server.
Bouncer IPS is a multimodular system. Every function has a component that is designed and specialized for some specific function. Bouncer IPS includes the following components:
- Bouncer Defence Unit (BDU)
- Bouncer Control Unit
- Bouncer Report Unit (BCU)
- Intelligence Plug-In
- Alarm Center Plug-In
- Bouncer Shield Plug-In
- Update Manager Plug-In
- Bouncer Inter-connection Channel (BIC)
Bouncer Defense Unit (BDU)
The Bouncer Defense Unit (BDU) is the core of the intrusion prevention system. Its defined policies determine the level of prevention protection.
The BDU is absolutely transparent – it does not affect network traffic – and can be deployed in different deployment methods.
It can also be placed on multiple network segments such as the perimeter, DMZ, and so forth.
The BDU can be either set up straightaway using the default set of policies or deployed after customizing the policies according to the
customer’s requirements.
Bouncer Control Unit (BCU)
The Bouncer Control Unit (BCU) is an intuitive and easy-to-use control center.
By selecting a BDU from the console, the security operator can set up, and monitor traffic, and query logs for all the BDUs in the system.
All the communication between the Bouncer and the BCU is through the transparent protocol (not TCP/IP), so as to maximize end-to-end security.
Bouncer Reporting Unit (BRU)
The Bouncer Reporting Unit (BRU) provides advanced drill-down capabilities integrated with a Crystal Reports engine.
The user-friendly report format provides comprehensive information for managers on both operational and tactical levels.
Bouncer Intelligence Center Plug
The Bouncer Intelligence Center Plug-In is responsible for aggregating attacker information during the attack.
Furthermore, it supports adaptive context building and triggering of various responses.
The intelligence plug-in is installed as a separate device for central intelligence gathering. The amount and type of target data collected are defined in the BDU security policies.
In addition, the intelligence plug-in provides high-quality graphic representations of both the attackers’ activity and the scale of the attack.
Alarm Center Plug-In
The Alarm Center Plug-In is responsible for consolidating and distributing arms to an array of alarm devices (mobile phones, pagers, email accounts, etc.).
It is installed as a separate device that consolidates alarms from different BDUs and disseminates alarm information between the BCU, BDUs, and designated personnel.
Bouncer Shield Plug-In
The Bouncer Shield Plug-In is responsible for updating and maintaining information on the current most suspicious targets. This information is obtained from reliable industry sources.
Update Manager Plug-In
The Update Manager Plug-In manages the Bouncer system updates such as versions, hotfixes, patterns, and security-related information for both the BCU and the BDUs.
Bouncer Inter-Connection Channels (BICs)
It provides seamless connections between the Bouncer IPS components (BDU, BCU, etc.).
The main reason for using multiple channels is to maintain reliable separation so that online activities are not disrupted by data probing or data distribution.
Configuring the IPS
The elements of the IPS configuration include the following.
- Enabling and disabling the IPS
- Vulnerability definitions
- IPS exceptions
- Initial definition configuration
- Resetting the configuration
Enabling and Disabling the IPS
You can turn on and off all IPS functionality. Disabling the IPS is equivalent to disabling all vulnerability definitions, although the definition configuration itself remains unchanged.
If you turn off the IPS and then turn it back on, the configuration settings of all the definitions will be the same as they were before you disabled the IPS.
Vulnerability Definitions
Each definition corresponds to a specific vulnerability and has a unique name (identifier).
A definition is defined by a blob of data and specifies a default response, which is the action that is recommended by Microsoft. One of the following two default responses is specified in each definition.
- Block and log. Block every malicious packet containing exploit code that corresponds to the definition by dropping the affected packet and resetting the connection if TCP is being used and creating a log entry that specifies the applicable definition for the event.
- Log. Create a log entry that specifies the name of the applicable definition for every malicious packet detected without blocking it.
You can configure the IPS to use the recommended default response (block and log malicious packets or only log them) specified in each definition or to log malicious packets that are detected and generate events without blocking the traffic for all definitions, or you can disable the IPS. If you disable the IPS, the responses of all definitions will be disabled.
Each definition also includes the date on which it was published. In addition, definitions may contain data for the following fields:
- Business Impact – The possible business-impact levels are low, medium, and high.
- Confidence – The possible confidence levels are low, medium, high, and perfect.
- Severity – The possible vulnerability severity levels are low, moderate, important, and critical.
- Risk Level – The possible risk levels are low, medium, and high.
- Related Bulletins – A list of related security bulletins published by the Microsoft Response Center.
- Protocol – The targeted protocol.
- Type – The possible types of malware are trojan, adware, spyware, botnet, and others.
The vulnerability definitions available to the IPS are listed at the Intrusion Protection System node in Forefront TMG Management. The definitions for the following categories are listed separately.
- Virtual Patching – These definitions are characterized by a unique name, the date on which they were published, a severity level, a response, a protocol, a business-impact level, a confidence level, and a list of related security bulletins.
- IM/P2P Blocking – These definitions are characterized by a unique name, the date on which they were published, a risk level, and a response.
- Malware – These definitions are characterized by a unique name, the date on which they were published, a risk level, a type, a response, and a protocol.
- Other – These definitions are characterized by a unique name, the date on which they were published, a response, and a protocol.
The IPS allows rapid development of vulnerability-based definitions that can be used until patches are deployed (as opposed to “exploit definitions” which need to be written for specific attacks).
Note that a definition is used to detect exploits of the corresponding vulnerability, while a patch removes the vulnerability from the software and renders the exploit code ineffective.
Vulnerability definitions contain the policy updates needed to identify and block new vulnerabilities in Microsoft products. IPS definition releases parallel with the Microsoft patch release process.
When a vulnerability is discovered, a Microsoft definition authoring team becomes responsible for writing the IPS definitions.
Definitions are associated with Microsoft Response Center bulletins, although in some cases they may be released before a bulletin is available. Definitions are packaged by a Microsoft response team and are distributed to Forefront TMG customers worldwide from Microsoft Update.
A definition is never removed from Forefront TMG. After a definition has been downloaded, it remains in Forefront TMG until Forefront TMG itself is uninstalled.
Even previous versions of definitions are kept in Forefront TMG, in case you encounter problems with the updated definition and want to roll back.
Definitions are obtained for the inspection services from Microsoft Update. Nitrogen can automatically check for new definitions and definition updates and download them periodically. Nitrogen computers can also be updated manually.
The Nitrogen update client detects definitions that it does not have, as well as any updated versions of existing definitions, and downloads the applicable packages.
After definitions are downloaded and processed, they are available for configuration by the administrator or the auto-activation policy.
You must subscribe to obtain definition updates for each service.
A definition can impose a policy that blocks RPC calls on a particular UUID, or blocks calls to a vulnerable function.
The administrative tasks for vulnerability definitions include configuring the schedule for updating them, activating their response, and defining exceptions for them.
IPS Exceptions
You can create lists of two types of exceptions that define sources and destinations of traffic that will be excluded from the IPS.
- Excluded IP addresses. The IP addresses included in specific network entities can be excluded from the IPS. In particular, non-HTTP traffic whose source or destination is an IP address included in the network entities listed in the global IPS exception list and HTTP traffic whose source is an IP address included in these network entities will not be scanned or in any way affected by the IPS. The network entities included in this list may be computers, computer sets, networks, network sets, subnets, and IP address ranges.
- Excluded domain name sets. A list of domain name sets can also be excluded from the IPS. HTTP traffic sent to destinations included in the domain name sets in this list will not be inspected or in any way affected by the IPS.
The list of excluded IP addresses and the list of excluded domain name sets apply to all definitions enabled.
Initial IPS configuration
When you run the Getting Started Wizard, you will be asked whether to enable the IPS. If you enable the IPS, you can select one of the following options:
- Use the Microsoft recommended default action included in each definition (block and log or just log traffic that matches the definition).
- Detect and report malicious traffic and events, but do not block any traffic.
You will also be asked to define a schedule for obtaining updates of the IPS definitions from Microsoft Update. The following types of schedules can be configured.
- Checking for updates every time a fixed user-selected time period elapses. This is the only option that allows checking for updates more than once a day.
- Checking for updates once every day at a user-selected time.
- Checking for updates only on specific user-selected days of the week.
- Never checking for updates automatically.
All of these initial IPS settings can be modified at any time in Forefront TMG Management.
Resetting the IPS configuration
At any time, you can modify the IPS configuration for all the IPS definitions that have already been downloaded. When you reset the IPS configuration, you can select one of the following options:
- Use the Microsoft recommended default action included in each definition (block and log or just log traffic that matches the definition).
- Detect and report malicious traffic and events, but do not block any traffic.
When you reset the IPS configuration for definitions that have already been downloaded, you can also apply the option selected to new definitions that will be downloaded.
Activity Statistics
The overall activity of the IPS is reported in the following two fields in the Forefront TMG activity statistics.
- Packets inspected by the IPS
- Packets blocked by the IPS
Scenarios
The Forefront Threat Management Gateway (TMG) IPS is designed to protect users in the following scenarios.
Edge Firewall – Outgoing Access
Internal clients access the Internet for both business and leisure purposes.
An internal user in your organization may access a malicious resource on the Internet that contains exploit code for a new vulnerability in a network protocol that is already known to Microsoft, but the patch has not yet been deployed on this user’s computer.
In this scenario, Forefront TMG serves as an edge firewall that inspects traffic initiated by internal clients to the Internet.
Forefront TMG already downloaded the vulnerability definition and terminates the session with a malicious Internet resource, so that the client is not infected.
In addition, the IPS may protect the client from vulnerabilities in non-browser applications such as Instant Messaging, or newsgroup reader (MS05-30 for example). The Forefront TMG administrator reviews logs and alerts and learns about the exploit attempt.
Edge Firewall – Publishing
The IT manager in the organization publishes an internal server to the Internet through Forefront TMG to allow partners and Internet users to access the resources that the organization provides.
Malicious clients on the Internet connect to the published server and attempt to use exploit code that takes advantage of a new vulnerability in a network protocol to attack the server.
As in the first scenario, the vulnerability is already known to Microsoft, but the patch has not yet been deployed on the published server.
Forefront TMG already downloaded the vulnerability definition and terminates the session initiated by the malicious client. The publisher server is not infected.
The Forefront TMG administrator reviews logs and alerts and learns about the exploit attempt.
Roaming clients
A corporate user connects to the corporate network using his home computer.
The home computer is infected with some new malware that contains an exploit for a known vulnerability and starts attacking other corporate computers through the VPN tunnel connection.
Forefront TMG already downloaded the vulnerability definition and terminates any session that is trying to infect the corporate network using an exploit of the vulnerability.
In addition, Forefront TMG detects that the VPN client has been compromised and disconnects the VPN connection with it.
Branch Office
The IT manager deploys Forefront TMG as a branch office firewall, connecting a remote office with the headquarters.
All the traffic between computers in the branch office and the headquarters goes through Forefront TMG.
An internal user brought his laptop to the branch office from home, where it was infected with a virus.
The virus infects other computers in the branch office but is stopped by Forefront TMG and does not contaminate the headquarters.
Host Intrusion Prevention Systems (HIPS)

A host intrusion prevention system (HIPS) is an approach to security that relies on third-party software tools to identify and prevent malicious activities
Host-based intrusion prevention systems are typically used to protect endpoint devices. Once the malicious activity is detected, the HIPS tool can take a variety of actions, including sending an alarm to the computer user, logging the malicious activity for future investigation, resetting the connection, dropping malicious packets, and blocking subsequent traffic from the suspect IP address.
Some host intrusion prevention systems allow users to send logs of malicious activity and fragments of suspicious code directly to the vendor for analysis and possible identification.
Most host intrusion prevention systems use known attack patterns, called signatures, to identify malicious activity. Signature-based detection is effective, but it can only protect the host device against known attacks.
It cannot protect against zero-day attacks or signatures that are not already in the provider’s database.
The second approach to intrusion detection establishes a baseline of normal activity and then compares current activity against the baseline. The HIPS looks for anomalies, including deviations in bandwidth, protocols, and ports.
When activity varies outside of an acceptable range — such as a remote application attempting to open a normally closed port — an intrusion may be in progress.
However, an anomaly, such as a sudden spike in bandwidth use, does not guarantee an actual attack, so this approach amounts to an educated guess and the chance for false positives can be high.
A third common intrusion-detection method uses stateful inspection to assess the actual protocols in packets traversing the network. The analysis is called stateful because the malware prevention tool tracks the state of each protocol.
For example, it understands how TCP and UDP packets can or cannot carry DNS, SMTP, HTTP, and other protocols — and what values should or should not be contained within each packet of each protocol.
Stateful protocol analysis looks for deviations from normal states of protocol content and can flag a possible attack when an unexpected deviation occurs.
Since stateful analysis is more aware of actual packet contents, the chances for false positives are somewhat lower than statistical anomaly detection.
HIPS products often focus on just one of the three approaches, though multiple approaches are sometimes used.
For example, McAfee’s Host Intrusion Prevention for Desktop and Dell’s Managed iSensor Intrusion Prevention System (IPS) service are just two offerings that rely on multiple approaches to intrusion prevention.
Network Intrusion Prevention System (NIPS)

A network-based intrusion prevention system (NIPS) is a system used to monitor a network as well as protect the confidentiality, integrity, and availability of a network.
Its main functions include protecting the network from threats, such as denial of service (DoS) and unauthorized usage.
The NIPS monitors the network for malicious activity or suspicious traffic by analyzing the protocol activity. Once the NIPS is installed in a network, it is used to create physical security zones.
This, in turn, makes the network intelligent and quickly discerns good traffic from bad traffic. In other words, the NIPS becomes like a prison for hostile traffic such as Trojans, worms, viruses, and polymorphic threats.
An intrusion prevention system (IPS) sits in line on the network and monitors the traffic. When a suspicious event occurs, it takes action based on certain prescribed rules.
An IPS is an active and real-time device unlike an intrusion detection system, which is not inline and is a passive device. IPSs are considered to be the evolution of the intrusion detection system.
IPS Approaches
Some of the approaches being used are
1. Software-based heuristic approach
This approach is similar to IDS anomaly detection using neural networks with the added ability to act against intrusions and block them.
2. Sandbox approach
Mobile code like ActiveX, Java applets, and various scripting languages are quarantined in a sandbox – an area with restricted access to the rest of the system resources. The system then runs the code in this sandbox and monitors its behavior.
If the code violates a predefined policy it’s stopped and prevented from executing, thwarting the attack (Conry-Murray).
3. Hybrid approach
On network-based IPS (NIPS), various detection methods, some proprietary including protocol anomaly, traffic anomaly, and signature detection work together to determine an imminent attack and block traffic coming from an inline router.
4. Kernel-based protection approach
Used on host-based IPS (HIPS). Most operating systems restrict access to the kernel by a user application. The kernel controls access to system resources like memory, I/O devices, and CPU, preventing direct user access.
In order to use resources, user applications send requests or system calls to the kernel, which then carries out the operation.
Any exploit code will execute at least one system call to gain access to privileged resources or services. Kernel-based IPS prevents the execution of malicious system calls.
Programming errors enable exploits like buffer-overflow attacks to overwrite kernel memory space and crash or take over computer systems.
To prevent these types of attacks a software agent is loaded between the user application and the kernel. The software agent intercepts system calls to the kernel, inspects them against an access control list defined by a policy, and then either allows or denies access to resources.
On some IPS systems, the agent checks against a database of specific attack signatures or behaviors. It could also check against a database of known good behaviors or a set of rules for a particular service.
Either way, if a system call attempts to run outside its allowed zone, the agent will stop the process.
Prevention Methods
1. Protecting System Resources Trojan horses
Trojan horses, rootkits, and backdoor salter systems resources like libraries, files/directories, registry settings, and user accounts. By preventing the alteration of system resources, hacking tools cannot be installed.
2. Stopping Privilege Escalation Exploits
Privilege escalation attacks try to give ordinary users root or administrator privileges. Disallowing access to resources, which alter privilege levels, can prevent this and block exploits like Trojan horses, rootkits, and backdoors.
3. Preventing Buffer Overflow Exploits
By checking whether the code about to be executed by the operating system came from a normal application or an overflowed buffer, these attacks can be stopped.
4. Prohibit Access To E-mail Contact List
Many worms spread by mailing a copy to those in Outlook‘s contact list. This could be halted by prohibiting e-mail attachments from accessing Outlook’s contact list.
5. Prevent directory traversal
The directory traversal vulnerability in different web servers allows the hacker to access files outside the web server’s range. A mechanism that would prevent the hacker access to the web server files outside its normal range could prevent such malicious activities. Unix’s has a chroot command that does this.
Full-featured IPS
The IPS Software Blade provides a complete Intrusion Prevention System security solution, providing comprehensive network protection against malicious and unwanted network traffic, including:
- Malware attacks
- Dos and DDoS attacks
- Application and server vulnerabilities
- Insider threats
- Unwanted application traffic, including IM and P2P
Important IPS Performance Metrics
IPS performance metrics are measured in terms of:
- Dynamic alerting capability
- Lower false positives
- Threat blocking capability
- High availability/ redundancy/ speed of working
- Ability to correctly identify attacks and drop packets accurately
Some IPS solutions offer the flexibility to implement different protection options (rules) for different segments of the networks, which is especially useful for large networks.
Some of them are capable of isolating the attack traffic to a network segment and limiting the bandwidth to reduce the effect of network threats. IPS helps identify and mitigate the following types of network threats.
Summary
Intrusion detection and prevention systems provide us with the first line of defense against malicious intruders. We must not consider an IPS as a substitute for IDS (it’s a different case if the same tool provides all the functions of both tools).
IPS and IDS provide the control and visibility required by any enterprise to protect its infrastructure from being attacked and taken over.
You can follow us on Linkedin, Twitter, and Facebook for daily Cybersecurity updates also you can take the Best Cybersecurity course online to keep yourself updated.
Other SOC Topics: