The field of computer Forensics analysis involves identifying, extracting, documenting, and preserving information that is stored or transmitted in an electronic or magnetic form (that is, digital evidence).
Forensics Analysis – Volatile Data:
- The data that is held in temporary storage in the system’s memory (including random access memory, cache memory, and the onboard memory of system peripherals such as the video card or NIC) is called volatile data because the memory is dependent on electric power to hold its contents.
- When the system is powered off or if power is disrupted, the data disappears.
How to Collect Volatile Data:
- There are lots of tools to collect volatile memory for live forensics or incident response. In this, we are going to use Belkasoft live ram Capture Tool.
- After the capture of live data of RANDOM ACCESS MEMORY, we will analyze it with Belkasoft Evidence Center Ultimate Tool.
Acquisition of live Volatile Memory:
Run the tool as an administrator and start the capture.
Dump File Format:
After the successful capture of live Ram memory. The file is will be saved in the .mem extension.
Evidence File Analyser:
Belkasoft Evidence Center Ultimate Tool to analyze volatile memory.
A forensic examiner or Incident Responder should record everything about the physical device’s appearance, Case number, Model Number of Laptop or Desktop, etc.
Click the Ram Image and enter the path of the .mem file which is a live ram dump file.
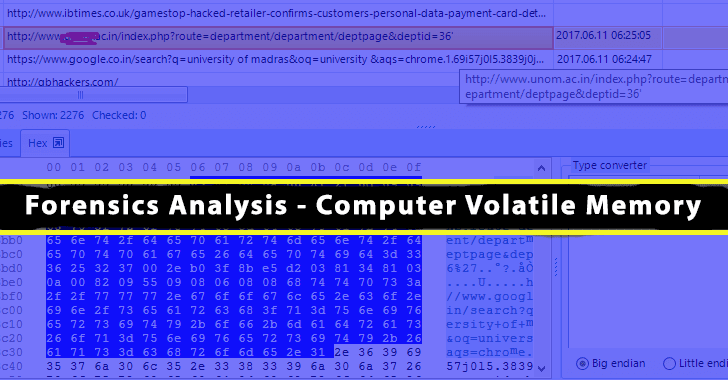
Malicious Activities on the Public Website
In the above picture, the attacker is trying for SQL Injection on Public Website.
Anonymous Vpn

In the above figure attacker installed and executed for hiding the source IP address.
Mail Inbox
The attacker has logged on with some public mail servers, and now forensic examiners are able to read inbox emails.
Recent File Accessed
Attackers last accessed file directory paths. The Forensics examiner will have priority to investigate this path for suspicious files.
Pictures
Recent Pictures downloaded from websites will be stored in the cache memory.
There are many relatively new tools available that have been developed in order to recover and dissect the information that can be gleaned from volatile memory.
This is a relatively new and fast-growing field many forensic analysts do not know or take advantage of these assets.
Volatile memory may contain many pieces of information relevant to a forensic investigation, such as passwords, cryptographic keys, and other data.
You can follow us on Linkedin, Twitter, and Facebook for daily Cybersecurity and Hacking New updates