Kali Linux recently released version 2024.1, the first release of the year 2024, with new Micro Mirror free software CDN, a theme refresh, additional Desktop environment changes, NetHunter updates, and four new tools.
Kali Linux is one of the most powerful Debian-based Linux distributions, developed and maintained by Offensive Security.
This operating system is based on Linux and is available for free and open-source, with two key goals to accomplish:
- Ethical Hacking
- Penetration Testing
A wide range of information security tools, such as those for security research, reverse engineering, penetration testing, red team testing, computer forensics, and vulnerability management, are included with Kali Linux.
You can analyze a malware file, network, module, and registry activity with the ANY.RUN malware sandbox, and the Threat Intelligence Lookup that will let you interact with the OS directly from the browser.
Kali Linux 2024.1 New Updates And Features
Launching The Micro Mirror Free Software CDN
The network of community mirrors for the Kali Linux distribution has been fortified with the launch of the Micro Mirror Free Software CDN.
One-liner, a network of mirrors devoted to providing Linux and Free Software, is the Micro Mirror CDN.
Micro Mirrors, which are machines with “only” a few TB of storage, are focused on hosting only the most highly demanded projects, in contrast to standard mirrors that hold about 50TB of project files.
To put it another way, they offer more bandwidth where it’s most required.
The FCIX Micro Mirror team handles all other tasks here, including purchasing the hardware, shipping it to the data center, and remotely managing it using their open Ansible playbook. The sponsor merely supplies the bandwidth.
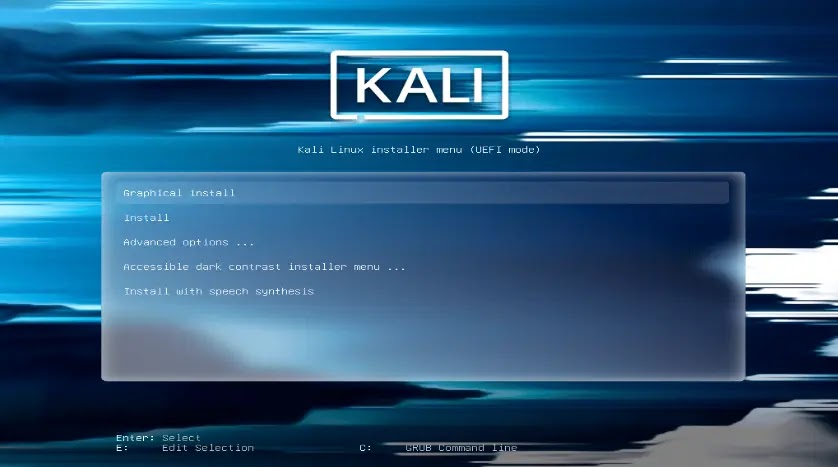
2024 Theme Refresh
Similar to earlier releases, this upgrade includes the annual theme refresh, a custom that keeps the tools and interface up to date.
This newest theme has been meticulously created to improve the user experience right from the start.
Including major improvements to the login screen, boot menu, and collection of eye-catching desktop wallpapers for both our regular Kali and Kali Purple versions.
.webp)
Desktop Changes
A useful improvement to the Xfce desktop is included in this latest release.
With one click, users can now quickly copy their VPN IP address to the clipboard, streamlining their workflow and increasing productivity.
Make sure xclip is installed on your system (sudo apt update && sudo apt -y install xclip) to benefit from this functionality.
This update makes managing your VPN connections on Kali Linux considerably easier to use and understand.
Other Xfce Changes:
- Kali-undercover updated to fix compatibility with the latest Xfce
- Fixed a bug with xfce-panel and Kali’s customized cpugraph plug-in
Gnome-Shell Updates
One significant modification to the Gnome desktop is the addition of eye-of-gnome (eog) image viewer with Loupe, continuing the transition to GTK4 based applications.
Furthermore, Kali’s repositories now have the most recent version of Nautilus file manager, which significantly improves file search efficiency and adds a redesigned sidebar.
.webp)
New Tools In Kali
Through the network repository, the following new tools were included in this Kali release:
- blue-hydra – Bluetooth device discovery service
- opentaxii – TAXII server implementation from EclecticIQ
- readpe – Command-line tools to manipulate Windows PE files
- snort – Flexible Network Intrusion Detection System
NetHunter Updates
The mobile penetration testing platform Kali NetHunter has been updated to support Android 14 and add new attack features.
.webp)
Icon Theme Update
A few more app icons have been added to provide a fully themed experience for Kali Linux default installations.
New symbolic icons were added to the icon set, which has improved uniformity throughout the system.
.webp)
How To Get Kali Linux 2024.1?
If you already have a Kali Linux installation, keep in mind that you may always perform a fast update:
.webp)
A quick check can be performed with the following commands.
.webp)
Moreover, you can visit the official website of Kali Linux to download the latest version of Kali Linux (Kali Linux 2024.1).
You can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits, with Perimeter81 malware protection. All are extremely harmful, can wreak havoc, and damage your network.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.



