A DNS Attack is a type of cyber attack that exploits the weakness or vulnerability in a Domain name system.
Today, the internet has turned into an integral part of our lives. From communicating to banking to shopping to traveling, every aspect of our lives is around the internet.
Since the internet has been widely used, cybersecurity is a primary concern for most web users as every now and then we hear the news about cyber attacks.
Nowadays, cyber attack is common. Even they are becoming a big headache for many IT companies and businesses.
In recent years, some big names such as Google, The New York Times, etc. have fallen victim to cyber-attacks.
In today’s post, we will come to know about DNS Attacks, how they work, and how to fight against them.
Table of Contents
What is a DNS Attack?
How does DNS work?
How Hackers Use DNS?
Types of DNS Attacks
DDoS Attack on DNS
Final Words
FAQ
1. What causes a DNS attack?
A DNS (Domain Name System) attack happens when someone uses flaws in the DNS system to stop, redirect, or steal network data.
DNS hacks can be caused by a number of things, such as bad security settings, old software, and weak authentication. DNS spoofing is a common type of DNS attack in which the attacker changes the DNS cache in order to send searches to a fake website.
2. What are common DNS attacks?
Common DNS attacks try to take advantage of flaws in the Domain Name System to stop regular internet services or send traffic to malicious sites.
Some of the most common types are DNS Spoofing (or DNS Cache Poisoning), in which an attacker corrupts a DNS resolver’s cache to send users to fake websites, DNS Hijacking, in which an attacker takes unauthorized control of a DNS server to redirect traffic, and DNS Tunneling, in which DNS requests are used to get around network security measures and smuggle out data.
There are also DoS and DDoS attacks, which target DNS servers to flood them with fake requests and make them unavailable.
3. Is DNS a security risk?
Domain Name System (DNS) is an important part of the internet because it helps translate human-readable domain names into IP addresses.
However, it was not originally made with strong security in mind. So, DNS can be a security risk if it is not controlled and protected properly. DNS attacks like DNS spoofing, DNS hijacking, and DDoS attacks against DNS services take advantage of weaknesses in the DNS infrastructure to disrupt or steal network traffic.
DNS is often the first place where web names are looked up, so if its security is broken, it could lead to data theft, service outages, or people being sent to malicious sites without their permission.
What is a DNS Attack?
Indeed, DNS attacks happen when a hacker is able to find weaknesses to exploit in the DNS (Domain Name System).
Hackers take advantage of vulnerabilities to make DNS attacks possible. In order to understand, how DNS attacks actually work, you will have to first understand how DNS works.
For those who don’t know, the domain name system is a protocol that interprets an alphabetic domain name into an IP address.
In short, its major function is to convert a user-friendly domain name into a computer-friendly IP address.
How does DNS work?
When a user types a domain name in the browser, a program available in the operating system known as DNSresolver searches for the IP address of that domain name.
First, the DNS resolver searches its own local cache and checks if it already has the IP address for that domain.
If it does not find it in the local cache, It queries a DNS server to check if it knows the accurate IP address for that domain.
DNS servers work in a loop which means they are able to query each other to find the DNS server that knows the correct IP address of the domain name.
As soon as the DNS resolver locates the IP address, it returns the IP address to the requesting program. DNS caches domain addresses for future use as well.
Though the Domain Name System is quite powerful it seems less focused on security. Maybe that’s why we are noticing different types of DNS attacks.
To minimize the possibility of DNS attacks, server administrators must take some necessary steps.
They can use an upgraded version of DNS software and regularly configure servers to duplicate. At a personal level, users can flush their DNS cache to avoid security risks. If you don’t know how to flush DNS, read a resourceful post at hostinger.com.
How Hackers Use DNS?
The biggest issue with the DNS system is that if on any account a hacker is able to find a way to replace the authorized IP address of a website with a rogue IP address, then any person trying to access that website will be sent to a bogus address.
The user would not have any idea that he was accessing the wrong address.
One of the major problems with the DNS server configuration is that it does not remember its default configuration. Attackers take advantage of this loophole.
Types of DNS Attacks
Over the past few years, a sudden increase has been noticed in DNS attacks. And this attack is not limited to small websites only.
Numerous popular websites such as Reddit, Spotify, and Twitter have also complained about their inaccessibility to thousands of their users.
As DNS attacks are becoming all too common, we should learn to identify DNS attacks so that we can tackle the situation better. Let’s have a look at the types of DNS attacks.
Zero-day attack- In this type of attack, the attacker exploits a formerly unknown vulnerability in the DNS server software or protocol stack.
Fast Flux DNS- Hackers swap DNS records in and out at high frequency to redirect DNS requests. This technique helps the attacker avoid detection as well.
DNS-Spoofing- DNS spoofing is also known as DNS cache poisoning. It is a type of computer security hacking.
Attackers or hackers corrupt the whole DNS server by replacing the authorized IP address with the bogus IP address in the server’s cache. This way they redirect the whole traffic to a malevolent website and collect the crucial information.
This is one of the most popular phishing techniques attackers use to steal information. Because users type the correct domain address in their browsers, they never realize that are accessing a fake or rogue website.
Therefore, it becomes challenging to detect this attack. Sometimes, users are not able to find it until the time to live (TTL) expires. TTL or time to live in the time till the DNS resolver remembers the DNS query before it expires.
The best method to prevent DNS cache poisoning attacks should be time to time clearing of DNS cache.
Also, you can read Top 10 Dangerous DNS Attack Types and The Prevention Measures
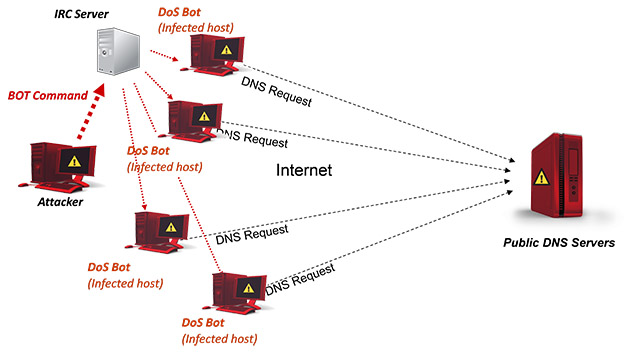
DDoS Attack on DNS
The DDoS attack is referred to as a Distributed Denial-of-service attack.
It usually arises when multiple systems flood the resources of a targeted system. Attackers can use this attack against different types of systems which include DNS servers as well.
A DDoS attack can crash the whole DNS server and make users unable to access the web. However, they will be able to access websites they have accessed recently if they are saved in the local cache.
DNS server attacks can be a huge network security issue. Therefore, it should not be taken lightly by businesses. They should implement state-of-the-art safeguards to reduce and prevent the effects of such attacks.
How you can defend against this attack depends on the role of your systems in the environment. However, you may take the following steps.
Get regular insight into what is actually going on in a network. You can take the help of technologies like IPFIX, NetFlow, etc. for the same.
DDoS attacks usually enter a network that has excessive packet-per-second rates. Think of some good solutions for it.
Final Words
In conclusion, DNS hacks use flaws in the Domain Name System, which is a key part of how the internet works, to stop services from working, steal data, or send traffic to malicious sites.
Given how important and widespread DNS is in networking, these kinds of attacks can have a wide range of effects. They can affect not only individual users but also businesses and even whole parts of the internet. DNS protection should not be taken lightly because of this.
To reduce risks, you need effective remedies like DNSSEC, software updates on a regular basis, and strong monitoring systems. Organizations should make DNS security a top priority as part of their overall cybersecurity strategy to protect their data, keep services running, and make sure their online platforms are safe and secure.
If DNS vulnerabilities aren’t fixed, they can cause a lot of operational, financial, and reputational damage, so it’s important to protect against DNS attacks in a proactive way.
Have you ever been a victim of a DNS attack? How did you prevent them? Do share your experiences with us.



