There are different OS for Hacking and Penetration Testing Linux distro is dedicatedly developed for Security Researchers or Ethical Hackers to perform various operations in security industries with a variety of hacking tools that are prebuilt with OS.
The Best Linux Distro Operating Systems are known for their stability, security, and flexibility.
These operating systems are highly reliable and rarely experience crashes or system failures. In addition, they have robust security features that protect against malware and hacking attempts.
Furthermore, Linux distros offer a wide range of customization options, allowing users to adapt the system to their specific needs and preferences.
Overall, the best Linux distro operating systems provide a seamless and efficient computing experience.
Linux is an open source it gives you the freedom to choose your own operating system.
For that, a lot of developers and companies developed some special distributions for this purpose. Ex: Kali Linux, BackBox Linux, ParrotSecurity OS, and so on!
Table of Contents
What is Linux Distro?
FAQ
Top 10 Best Linux Distro Operating Systems
1. Kali Linux
2. Parrot Security OS
3. BackBox Linux
4. BlackArch Linux
5. Pentoo
6. Samurai Web Testing Framework (Samurai-WTF)
7. Network Security Toolkit (NST)
8. WifiSlax
9. Bugtraq
10. Cyborg Hawk
Conclusion
What is Linux Distro?
The Linux kernel, together with additional system utilities, libraries, desktop environments or window managers, and extra software applications, are all part of a Linux distribution (sometimes known as a “distro”).
Linux distributions are built to give users a unified and fully functional OS that can be installed and used for a wide range of tasks.
Each Linux distribution is a slightly modified version of the Linux OS that is designed to work best in a particular set of circumstances. To better understand Linux distributions, consider the following:
Variety: There are hundreds of Linux distributions, each with its own set of tools, software options, and philosophy on how things should be built.
It’s possible to find distributions designed for certain tasks, such as server administration, multimedia creation, security auditing, or minimal system requirements.
Components: The Linux kernel is the backbone of any Linux distribution, together with libraries, utilities, command-line tools, graphical user interfaces, and other applications. Distributions may use a wide variety of component options.
Desktop Environments and Window Managers: The style and feel of the graphical user interface can be customized with a variety of desktop environments and window managers, which are available in many Linux variants.
Some of the most well-liked desktop environments are GNOME, KDE Plasma, Xfce, and LXQt.
Package Management: Software installation, upgrades, and removals are all handled via package management systems in Linux distributions.
Pacman (Arch Linux), YUM/DNF (Fedora/CentOS), and APT (Debian/Ubuntu) are all examples of package managers.
Customization: The preferences of the distribution’s maintainers and intended users might be heavily incorporated into the distribution’s design.
This includes picking out things like the default apps, desktop theme, and other settings.
Support and Community: In most cases, you can count on receiving help, documentation, and support from the distribution-specific user community. The Linux ecosystem relies heavily on its strong feeling of community.
FAQs – OS for Hacking
1. What makes these Linux distros suitable for ethical hacking and penetration testing?
These Linux distros are specifically designed and developed with tools and features that are essential for ethical hacking and penetration testing purposes.
They come pre-installed with various security and penetration testing tools, making them convenient and efficient for cybersecurity professionals.
2. Can I use these Linux distros if I’m not an ethical hacker or penetration tester?
Absolutely! While these Linux distros are primarily designed for ethical hacking and penetration testing purposes, they can also be used by cybersecurity enthusiasts, students, or anyone interested in learning more about cybersecurity.
3. Which Linux distro is the most popular for ethical hacking and penetration testing?
Kali Linux is widely considered the most popular Linux distro OS for hacking and penetration testing.
It is extensively used and has a large community of users and developers, providing extensive documentation and support.
4. Can I dual-boot these Linux distros with my existing operating system?
Yes, you can dual-boot these Linux distros with your existing operating system. Most of them offer the option to install alongside other operating systems during the installation process.
5. How many Linux distros are there?
Since some distributions may be started and stopped over time, the precise number may change.
The open-source nature of Linux allows developers to modify and create their own variations of the operating system to cater to unique needs or preferences, which explains a large number of distributions.
There are many Linux distributions available, but some of the most popular ones are Ubuntu, Debian, Fedora, CentOS, Arch Linux, and openSUSE.
In addition, there are distributions tailored to particular uses, like security, gaming, multimedia development, and instruction.
6. What are the advantages of Linux?
Linux is open-source software, which means that anyone can get its source code for free. This makes it easier for people to work together and share information, and it lets users change and share the software without having to pay licensing fees.
Linux is very easy to change. Users can build a computer environment that fits their needs and tastes by choosing from a wide range of distributions, desktop environments, and software packages.
7. What is Linux structure?
The term “Linux structure” can be used to refer to a number of distinct features of the Linux operating system, including the hierarchy of its file system, the architectural components of the system, and the organizational structure of the system.
Best Linux Distro Operating Systems
| Best OS for Hacking & Penetration Testing | Key Features |
| Kali Linux | GNOME as a Desktop Environment Ranked number one in Top 10 |
| Parrot Security OS | Excellent GUI interface Big repository |
| BackBox Linux | XFCE as a Desktop Environment Most professional |
| BlackArch Linux | 2500 hacking tools Almost it covers all the phases of cybersecurity |
| Pentoo | Nice collection of hacking tools |
| Samurai Web Testing Framework (Samurai-WTF) | Best OS for Hacking Based on Ubuntu |
| Network Security Toolkit (NST) | Professional best OS for Hacking Based on Fedora |
| WifiSlax | Lot of Wifi Cracking/Hacking/PenTesting tools Deployed with the corporate network |
| Bugtraq | Based on Debian |
| Cyborg Hawk | Ubuntu-based best OS Amazing distro for hacking purposes |
Top 10 Best OS for Hacking & Penetration Testing
1- Kali Linux:
Core Features:
- GNOME Shell
- KDE Plasma
- Xfce is a lightweight desktop environment
Kali Linux is the #1 Best OS for Hacking and Penetration Testing Distribution based on Debian. Developed by Offensive Security.
The first release was on February 5, 2006, it’s a completion of the BackTrack Linux Project.
There are 100’s of hacking tools that are pre-installed with Kali Linux for various operations such as pen testing, malware analysis, forensic analysis, information gathering, networking scanning, exploitation, etc.
It used to use GNOME as a Desktop Environment. Nowadays Kali Linux has become a Rolling release Distro.
It has a lot of tools in the Kali Repositories. Kali Linux Ranked number one in the Top 10 Penetration Testing & Ethical Hacking Linux 2020.
You can find the complete Kali Linux Tools & Tutorials here.
To Whom it is advised?
Cybersecurity professionals, ethical hackers, and IT administrators who need advanced penetration testing, security auditing, and system administration capabilities should use Kali Linux.
The toolkit includes hundreds of security research, computer forensics, reverse engineering, and vulnerability assessment tools. Information security and ethical hacking students benefit from Kali Linux.
It takes a thorough understanding of network and system security to use its tools, therefore beginners and those searching for a general-purpose Linux distribution should not use it. Kali Linux utilities can be dangerous if misused.
2- Parrot Security OS:
Core Features:
- Raspberry Images
- WSL Edition
- Architect Edition
Parrot Security is #2 and another Best OS for Hacking and Penetration Testing, Forensics Distro is dedicated to Ethical Hackers & Cyber Security Professionals.
Parrot OS equally contributes to the security community the same as Kali Linux with a variety of hacking tools and an excellent GUI interface.
It has a big repository that collects a lot of amazing hacking tools for newbies and experts. Developed by FrozenBox.
The first release was in June 2013. It used to use MATE as a Desktop Environment it’s based on Debian like Kali Linux.
To Whom it is advised?
Cybersecurity specialists, ethical hackers, penetration testers, digital forensics, and cryptographers should use Parrot Security OS.
A complete suite for advanced users who need tools for security auditing, penetration testing, computer forensics, reverse engineering, privacy, and coding. Due to its many educational tools, Parrot Security OS is appropriate for cybersecurity students and teachers.
Although user-friendly and suitable as a daily driver, it’s not suggested for Linux newcomers or those who need a general-purpose operating system.
The OS requires network and computer security knowledge to use its tools responsibly.
3- BackBox Linux:

Core Features:
- Red Team Simulation
- Threat Intelligence
- ISO Hybrid with UEFI support
Backbox Linux is the #3 best OS for Hacking for ethical hacking and penetration testing distro based on Ubuntu Linux.
Developed by the BackBox Team. The first release was on September 9, 2010.
Backbox used to use XFCE as a Desktop Environment and Ubuntu LTS versions as a base.
It contains the most professional, famous, and used tools in the pen-testing field like MSF, NMAP, BurpSuite, Armitage, SQLMap, and so on.
To Whom it is advised?
Ethical hackers, penetration testers, security researchers, and cybersecurity experts should use BackBox Linux. Its compact, quick, and easy-to-use environment includes a full complement of security and penetration testing tools.
These tools aid network analysis, vulnerability assessment, and exploitation. Due to its user-friendly design and well-organized menus, BackBox is ideal for cybersecurity and ethical hacking students.
However, common users or Linux newcomers looking for a simple, daily operating system should avoid it. Effective and secure use of the platform requires network security and system management experience.
4- BlackArch Linux:

Core Features:
- XFCE Desktop Environment
- multiple window managers
- 2500 hacking tools
Black Arch Linux-based Arch Linux #4 Lightweight and best OS for Hacking for ethical hacking and Penetration Testing Distro designed for Professional and elite Hackers who can work with Linux like a Pro.
Black Arch contains nearly 2500 hacking tools and almost it covers all the phases of cybersecurity.
Used to use Fluxbox & OpenBox as a Desktop Environment with other DEs. It has huge tools in the repository more than 1500+ hacking tools included in the Distro & Repo. The first release was in 2013.
To Whom it is advised?
BlackArch Linux is recommended for cybersecurity experts, ethical hackers, and information security researchers. It is a dedicated Linux distro for penetration testing and security research with many tools for network analysis, vulnerability detection, and exploitation.
BlackArch is best for cybersecurity and Linux experts due to its complex nature and large toolset (over 2000).
The distribution demands extensive network security and system management knowledge, hence it is not intended for ethical hacking or Linux beginners.
Unfortunately, its complexity and specialized nature make it unsuitable for mainstream computing or a simple Linux experience.
5- Pentoo:
Core Features:
- Kernel with wifi hacking related packages
- Module loading support ala slax
- OPENCL cracking support
Pentoo is the #5 best OS for Hacking and pen-testing distro based on Gentoo. Nice collection of hacking tools. The first release was in June 2005. It’s somehow an old distro. We can say it’s outdated.
To Whom it is advised?
Pentoo Linux is suggested for ethical hackers, cybersecurity enthusiasts, and information security and penetration testers. It is a Gentoo-based Linux distribution featuring several security, penetration, and vulnerability assessment tools.
Those who enjoy Gentoo’s flexibility and configurability like Pentoo’s rolling release strategy, which provides the latest security tools and upgrades.
The Gentoo Foundation makes Pentoo difficult for newcomers and those unfamiliar with Gentoo. It’s great for Linux experts and command-line users who can customize computers.
Thus, it’s not suggested for general users or Linux or cybersecurity beginners.
6- Samurai Web Testing Framework (Samurai-WTF):

Core Features:
- SQLMap
- OWASP Zed Attack Proxy
- OWASP Juice Shop
Samurai WTF is one of the best OS for Hacking and Professional Web Application Penetration Testing frameworks and distro.
It contains only WebApp Pentest Tools such as Burpsuite, SQLMap… and so on. Based on Ubuntu. The first release was in 2008.
To Whom it is advised?
Web application developers, security professionals, and ethical hackers who specialize in web application security should use the Samurai Web Testing Framework (Samurai-WTF).
It’s a pre-configured package of tools for web application testing and analysis, making it suitable for web penetration testing, security assessments, and vulnerability discovery.
Web security mapping, discovery, exploitation, and reporting solutions are available from Samurai-WTF.
It’s not recommended for cybersecurity beginners or those unfamiliar with web application technologies and security. The framework assumes web application design and common security vulnerabilities can be understood.
It’s also not for general computing or non-web security users.
7- Network Security Toolkit (NST):

Core Features:
- NST Network Interface Bandwidth Monitor
- Network Security Toolkit
- Multi-Tap Network Packet Capturing
Network Security Toolkit also known as NST is the Professional best OS for Hacking and penetration testing and is also designed for Network Security and network Penetration Testing Operations. Based on Fedora.
It contains the most professional & used tools in the Network PenTest field. The first release was in 2003.
To Whom it is advised?
Network administrators, cybersecurity professionals, and ethical hackers who monitor and secure networks should use the Network Security Toolkit (NST).
This Linux-based live DVD/USB Flash Drive toolkit has many network traffic analysis, intrusion detection, network packet capture, and vulnerability assessment capabilities.
For network security analysis, diagnostics, and monitoring, NST provides graphical tools and reports to simplify network activities.
It can be useful for students and newcomers to network security, but its sophisticated features and extensive analysis are best used by experts who understand network protocols and security.
Without network management or cybersecurity experience, NST may not be suited for general computing purposes.
8- WifiSlax:
Core Features:
- Security and forensics tools
- Integration of various network drivers
- Live CD functionality
Wifislax is an amazing & best OS for ethical hacking and Wi-Fi penetration Testing Distro based on Ubuntu.
It contains a lot of Wifi Cracking/Hacking/PenTesting tools. Developed by an Italian Security Team.
It is mainly deployed with the corporate network to make sure employees access the protected network.
To Whom it is advised?
Cybersecurity specialists, ethical hackers, and wireless network security and testing managers should use Wifislax.
This Linux-based package provides network sniffing, encryption cracking, and vulnerability exploitation tools for Wi-Fi network audits and security.
Wifislax is used for doing penetration testing and security assessments on wireless networks, including Wi-Fi, Bluetooth, and RFID.
Its extensive features and functionalities are better for users who understand wireless networking ideas and security protocols, but it might be useful for network security students and hobbyists.
It takes expertise to operate Wifislax safely and successfully, thus it’s not for beginners in network security.
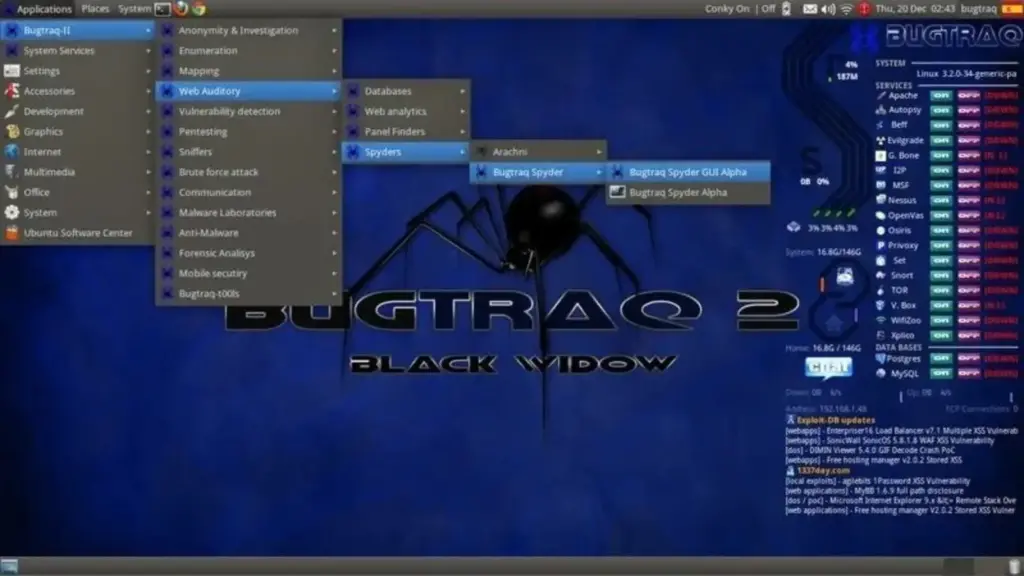
9- Bugtraq:
Core Features:
- GSM Forensics
- GNU/Linux distribution
- Malware Laboratories
Bugtraq professional penetration testing distro designed for Penetration Testing Operations and Reverse Engineering and Malware Analysis Missions. Based on Debian, contains a lot of hacking tools.
Developed by Bugtraq Team, the first release was in 2012. Download.
To Whom it is advised?
Bugtraq is recommended for ethical hackers, penetration testers, IT security experts, and cybersecurity researchers.
It’s a complete Linux distro including security audit, penetration testing, forensic analysis, and reverse engineering tools.
Bugtraq is adaptable for security jobs because it supports numerous architectures and provides cybersecurity-specific solutions.
A user-friendly interface and well-organized toolset make the distribution suitable for both experienced and inexperienced professionals.
However, cybersecurity fundamentals are still needed. It’s not advised for general computing users or IT security novices.
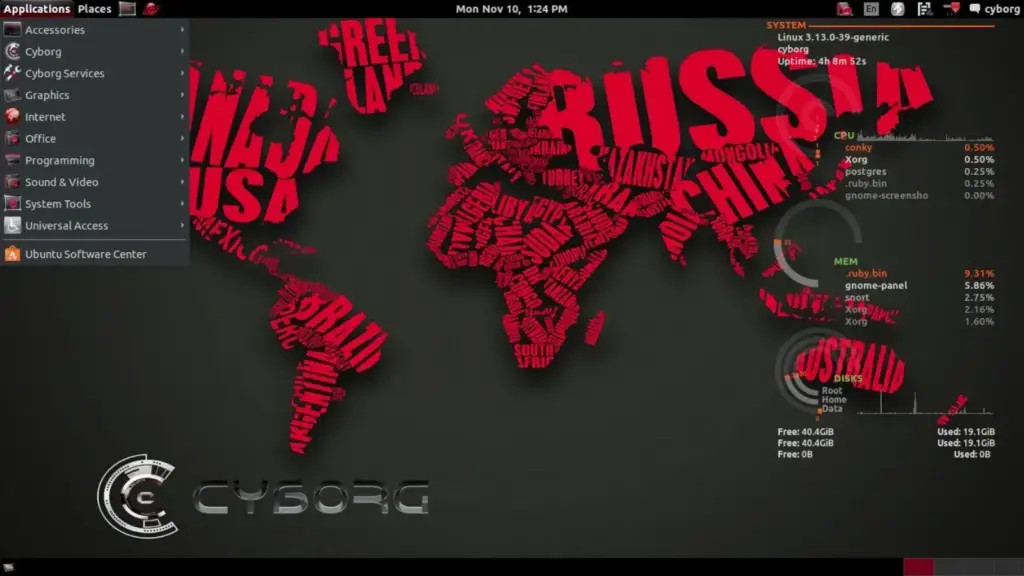
10- Cyborg Hawk:
Core Features:
- Full virtual machine support
- Patched kernel from injection
- Can be used as a live OS with full capability
Cyborg Hawk, the Ubuntu-based best OS for ethical hacking and penetration testing. Contains more than 700 hacking tools.
Amazing distro for hacking purposes. Developed by the Cyborg Hawk Team from Australia.
To Whom it is advised?
Cybersecurity specialists, ethical hackers, penetration testers, and forensic investigators should use Cyborg Hawk Linux.
It’s an Ubuntu-based distribution containing many cybersecurity tools for penetration testing, forensics, reverse engineering, and security research.
Cyborg Hawk’s user-friendly interface and comprehensive toolset make it suited for both seasoned cybersecurity professionals and beginners who want to learn by doing.
Though user-friendly, it demands a basic awareness of cybersecurity ideas and practices. Cyborg Hawk is not advised for basic computing or non-cybersecurity users due to its specialist nature.
Conclusion
Choosing the best OS for Hacking & penetration testing is a good sign to learn ethical hacking and Penetration testing concepts to enhance your skills and protect enterprise assets from cybercriminals.
When it comes to hacking or penetration testing, it’s important to remember that ethical hacking and security testing should only be done with the right permission and by all laws and rules.
It is against the law and bad manners to hack without permission. So, if you want to use an operating system for ethical hacking and security tests, you can choose from several Linux distributions that are made for these tasks.
Every security professional has their favorite security OS to make use of hacking tools for both learning and commercial purposes.
you can try all the OS at least once to experience the great feature.


-1.webp?w=218&resize=218,150&ssl=1)
-1.webp?w=218&resize=218,150&ssl=1)

.webp?w=218&resize=218,150&ssl=1)
