Group-IB has released its latest report, “Hi-Tech Crime Trends 2023/2024,” highlighting critical global cyber threats.
The report reveals a concerning trend where over 225,000 compromised ChatGPT credentials are being sold on dark web markets, posing security risks for businesses.

Key Points:
- Cyber Threat Landscape: The report emphasizes the growing collaboration between ransomware and Initial Access Brokers (IABs), leading to a surge in cyber threats globally.
- AI Integration: Cybercriminals are leveraging artificial intelligence (AI) technologies like large language models (LLM) such as ChatGPT to develop sophisticated malware and enhance their operational efficiency.
- Dark Web Sales: Group-IB detected a substantial number of compromised ChatGPT credentials for sale on illicit dark web platforms, with over 225,000 logs available from January to October 2023.
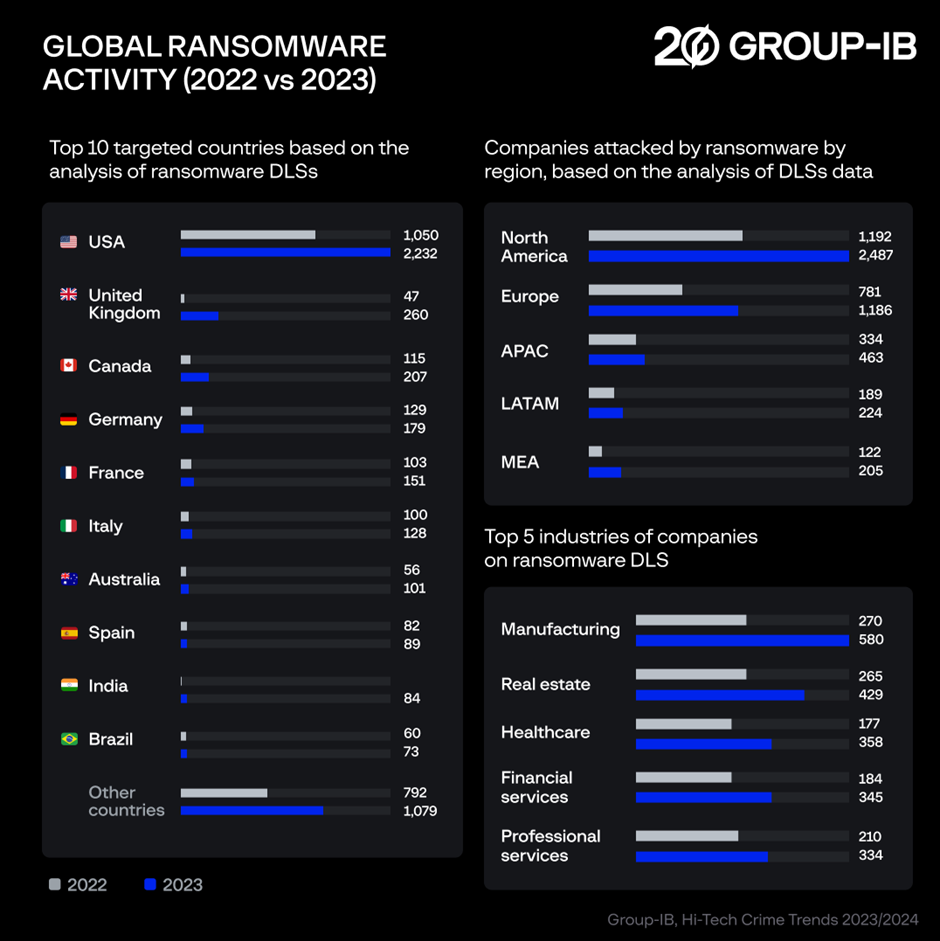
- Ransomware Activity: The report highlights a significant increase in ransomware attacks, with 4,583 companies having their data published on ransomware Dedicated Leak Sites (DLS) in 2023.
- APT Attacks: Nation-state-sponsored threat actors, known as Advanced Persistent Threat (APT) groups, targeted various regions globally, with the Asia-Pacific region being a major battleground.
Are you from SOC and DFIR teams? – Join With 400,000 independent Researchers
Malware analysis can be fast and simple. Just let us show you the way to:
- Interact with malware safely
- Set up virtual machine in Linux and all Windows OS versions
- Work in a team
- Get detailed reports with maximum data If you want to test all these features now with completely free access to the sandbox: ..
Rise of AI in Cyber Threats
Group-IB’s report, which has been a critical resource for fighting digital crime for over a decade, has, for the first time, included a section on AI and its implications for cybersecurity.
The report details how AI technologies, including large language models like ChatGPT, are being exploited by cybercriminals to develop malware, brainstorm new tactics, techniques, and procedures (TTPs), and enhance social engineering attacks.
The United States was the most common target for ransomware groups, as 1,060 US-based companies were the subject of ransomware DLS posts in 2023. The next most affected countries were Germany (129), Canada (115), France (103), and Italy (100).
The majority of these compromised accounts were breached by the LummaC2 information stealer, indicating a targeted approach by cybercriminals to exploit ChatGPT’s growing popularity in the professional sphere
Ransomware and Initial Access Brokers: A Persistent Threat
The report also sheds light on the persistent threat posed by ransomware and Initial Access Brokers (IABs).
In 2023, Group-IB’s Threat Intelligence unit detected a 74% increase in the number of companies that had their data published on ransomware-dedicated leak sites (DLS).

IABs, skilled at exploiting security vulnerabilities, continue to facilitate ransomware attacks by selling unauthorized access to networks.
The average price for corporate access dropped by 27% in 2023, suggesting an increase in the number of sellers and a competitive market.
Group-IB’s latest report underscores the evolving nature of cyber threats and the critical role AI is playing in this landscape.
The sale of compromised ChatGPT credentials on the dark web is a stark reminder of the importance of cybersecurity vigilance.
As AI continues to be integrated into corporate environments, the potential for misuse by cybercriminals grows, making it imperative for organizations to strengthen their defenses against these emerging threats.
You can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits, with Perimeter81 malware protection. All are incredibly harmful, can wreak havoc, and damage your network.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
%20(1).webp?w=696&resize=696,0&ssl=1)


