A hacker group compromised Russia’s Secret Intelligence Agency and they gained access to terabytes of data stored by the FSB contractor that includes the secret project details.
BBC learned that hackers who breached Russian intelligence contractor found that they are working towards cracking Tor browser as part of their secret project. It is still unclear how successful it will be, it heavily depends on the luck matching to Tor users activity.
How they Crack Anonymous Tor Network
SyTech came up with a project dubbed Nautilus-S to deanonymizing Tor traffic, the project employees a method of taking part in the Tor network as an exit node, to determine the website user connecting to.
ISP can able to identify that user connected with the Tor network, but not able to identify the website visitors used.
By combining both the data, from the ISP and Tor Exit node to “determine which sites are visited at what times, theoretically, help to identify someone – if they are lucky and the person randomly exits the network through their node.”
Systech also to carry out the man in the middle attack to replace the web page that to be visited by users. Tor is browser is very popular in Russia after Iran. Here is the list of top-10 countries by relay users.
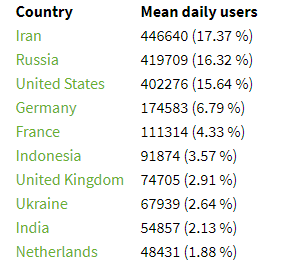
Tor project spokesperson said BBC that, “although malicious exit nodes could see a fraction of the traffic exiting the network, by design, this would not be enough to deanonymize Tor users. Large-scale effective traffic correlation would take a much larger view of the network, and we don’t see that happening here.”
Other Secret Projects
Nautilus
Unlike the previous project, Nautilus named without C developed a period of work (2009-2010) and their cost (18.5 million rubles) is to planned to collect data on social networks such as Facebook, MySpace, and LinkedIn.
Reward
A project that woked by SyTech from 2013 through 2014, in which Saitek tried to find a vulnerability in the BitTorrent network protocol.
According to the Document Sytech had to explore “the possibilities of developing a complex of penetration and covert use of peer-to-peer and hybrid networks,”
Mentor
SyTech’s other project called “Mentor” was designed for 2013-2014, to monitor email at the customer’s choice.
“According to the documentation provided by the hackers, the Mentor program can be configured so that it checks the mail of the required respondents at a specified time interval or collects the “mining group” using the specified phrases.”
Hope / Tax-3
Project on how Russia’s internet connects to and interacts with the outside network – and how to keep sensitive information safe.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity updates also you can take the Best Cybersecurity course online to keep yourself updated.



