Tor Browser 14.0 has been officially launched. It brings significant updates and new features to enhance user privacy and browsing experience.
This release is built on Firefox ESR 128, integrating a year’s worth of updates and improvements from Firefox while also addressing over 200 issues identified during the annual ESR transition audit.
New Features for Android
One of the standout features in Tor Browser 14.0 is the introduction of the “New circuit for this site” option for Android users.
Previously, Android users could only refresh all circuits through a workaround involving a persistent notification.
National Cybersecurity Awareness Month Cyber Challenges – Test your Skills Now
This new feature allows users to request a new circuit directly from the app’s menu, providing a more targeted approach without resetting their entire identity.

The browser also inherits updated typography from Firefox, featuring heavier headings and adjusted line heights for better accessibility.
Additionally, improvements have been made to enhance the usability and compatibility of fingerprinting protections, allowing features like picture-in-picture and screenshots without compromising privacy.
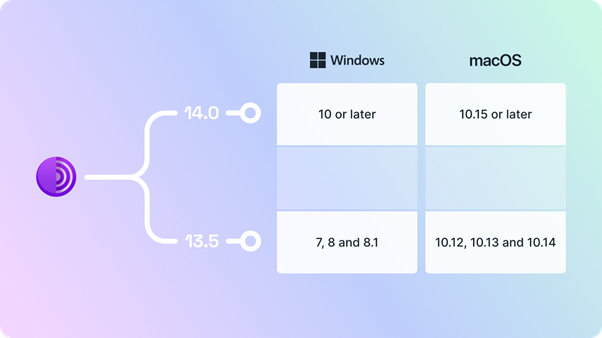
Initially, it was announced that Tor Browser 13.5 would be the last major release supporting Windows 7, 8, and 8.1, as well as macOS versions 10.12 to 10.14.
However, because Mozilla has extended support for Firefox ESR 115, these platforms will continue receiving critical security updates until at least March 2025.
This means users on these older systems will remain on Tor Browser 13.5, while those on newer platforms will be updated to version 14.0.
The development team faced numerous technical challenges during this release cycle.
They successfully unified the Android codebase into a mono repo, addressed reproducibility issues in Android APK generation, reduced APK size for x86 and x86_64 platforms, and improved user agent spoofing techniques.
As with any major release, there are known issues that users should be aware of. Android users who installed Tor Browser via Guardian Project’s F-Droid repo may face difficulties updating due to an unresolved issue with the repository.
These users can download the update directly from the Tor Browser website or use Google Play.
On Windows, running Tor Browser in compatibility mode can cause it to mistakenly identify the system as Windows 7, preventing updates to version 14.0. Users need to ensure compatibility mode is turned off before proceeding with the update
Tor Browser 14.0 marks a significant step in enhancing user privacy and functionality across platforms.
With new features for Android users and extended support for legacy systems, it continues to provide robust protection against tracking and surveillance while offering improved usability features.
Free Webinar on How to Protect Small Businesses Against Advanced Cyberthreats -> Watch Here



